If you have experience with exploitation on unix/linux machines, you will be familiar with exploit payloads (shellcode) that do little more than make a syscall to execve(), or a similar function. Unfortunately, we have no such luck with windows. The reason is the system call specification is not consistent across versions and service packs. For example, if you develop an exploit for MyExploitableApp v3.0.1 on windows xp service pack 2 which makes a call to execve(), when run on windows xp sp 3 might make a call to exit(). This kind of unreliability makes the windows system call interface much less useful for exploit development.
However, windows boxes are everywhere, and understanding windows exploitation is absolutely a requirement for a well-rounded exploit developer. The aim of this post is not to teach you about how windows exploitation works. That is a topic which has been well covered by authors much more competent than myself.
So, what is this article about? This article is about mona.py (hereon referred to as “mona”). Mona is a PyCommand (think extension) for Immunity Debugger. It is an amazing tool written by the guys over at corelan.be, and the download links are here (This is a link to the downloads page, I suggest you get the latest stable release. At the time of writing, this is version 1.1).
You should use this article to help yourself with mona.py as you learn to write exploits on windows. You will be much better off integrating the functionality of mona.py into your exploit development toolkit from the get-go, rather than trying to learn it later. Mona is extremely robust compared to most plug-ins, and it’s feature list can be overwhelming at first. Mona also requires a small amount of configuration before you can start using it. These are the kind of things I’d like to talk about in this post, as well as stepping through a real-world example.
If you are having trouble understanding why modules like this are helpful, don’t worry. I had trouble too. Generally speaking, exploitation deals with large regions of memory, lots of hexadecimal data. As exploit developers, we are looking for tiny little details and flaws in this information. We are better off trying to automate the process, since human error rates are high when dealing with binary and hex. Mona can scan data for patterns much faster and more accurately than we can. Mona can even build rop structures.
After you’ve downloaded and installed Immunity Debugger, move mona.py over to C:\program files\Immunity Inc\Immunity Debugger\PyCommands\ directory. Open Immunity Debugger.
Get in the habit of keeping mona up to date when opening up Immunity Debugger. Since this is an exploit writing tutorial, I will assume you understand the risks of running outdated software. To do this, run the following command:
!mona update
By default, this command uses HTTP Secure. If you are having difficulties with https communication you can force an http request with the following:
!mona update -t http
You can also switch between the stable (release) and unstable (trunk) packages with the following commands:
!mona update -t release
!mona update -t trunk
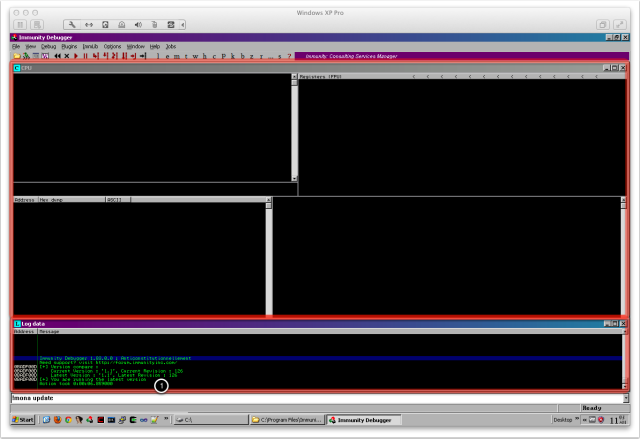
Below you can see how I set up the windows in Immunity. We are going to need the log screen quite often. Mona outputs to files, but the logs will help us along the way. I put it right below the CPU window. The two windows are highlighted below. As you can see in (1), mona.py is working properly inside Immunity Debugger, and this is how we can interact with it.
The next piece of this tutorial will cover mona’s initial configuration. It is a quick process, but a deep understanding of what you are doing is extremely important. The last thing you want is for a misconfigured mona.py to overwrite a file containing a recently found return address / pop pop ret.
Additional Links:
Immunity Debugger: http://immunityinc.com/products-immdbg.shtml
Corelan homepage: http://corelan.be
Corelan Mona project: http://redmine.corelan.be/projects/mona
Corelan unabridged Mona manual: https://www.corelan.be/index.php/2011/07/14/mona-py-the-manual/